Certified Liveness Detection and Voice Verification Systems: A New Era of Digital Security
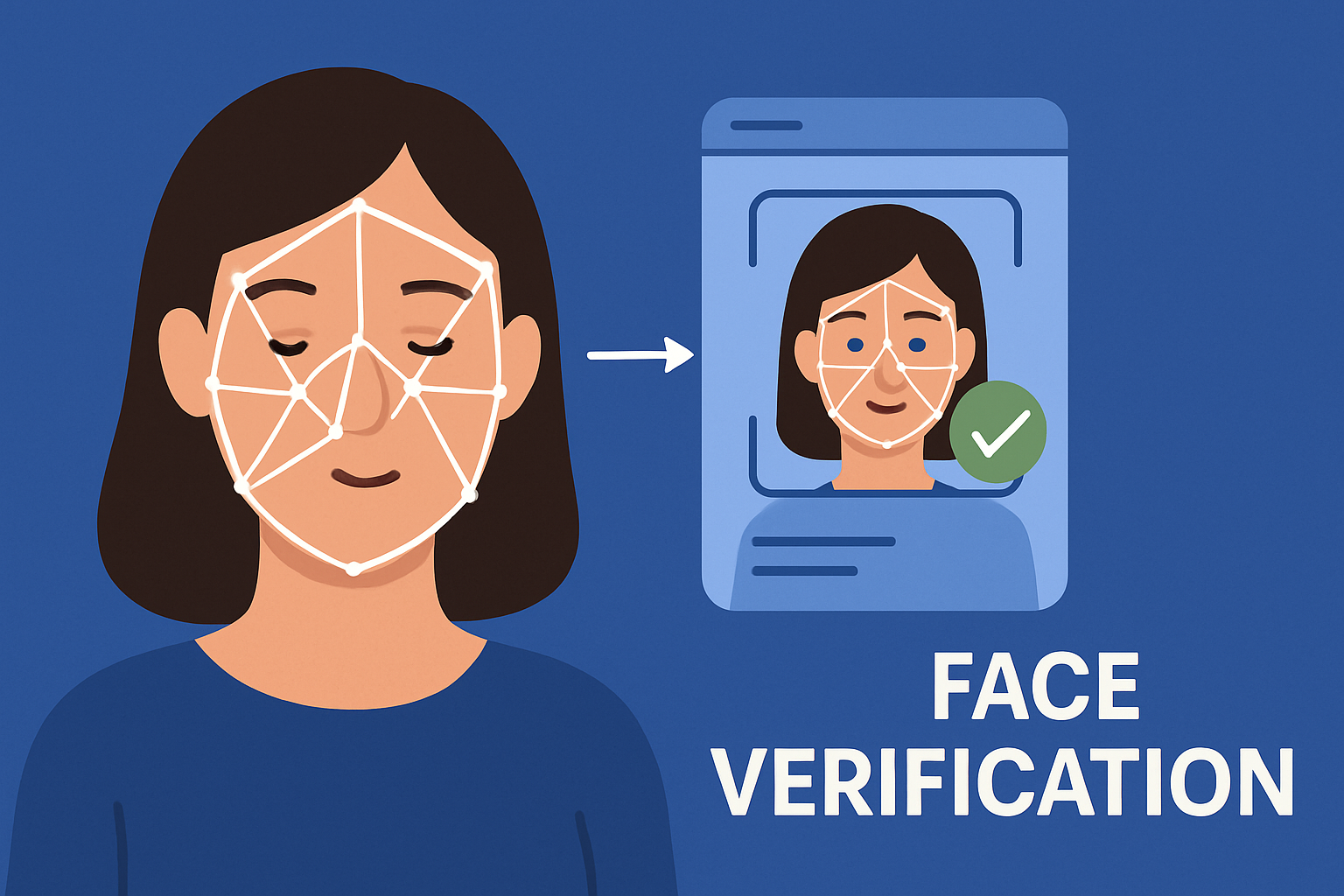
In today’s digital-first world, the need for robust and foolproof identity verification has never been more critical. As cyber threats and identity fraud continue to evolve, businesses are adopting advanced biometric technologies like certified liveness detection and voice verification systems to secure user authentication processes.
What is Certified Liveness Detection?
Certified liveness detection is an advanced biometric security method that ensures the user being authenticated is physically present in real time. Unlike traditional facial recognition, liveness detection prevents spoofing attempts using photos, videos, or 3D masks. Certified solutions are tested and validated by third-party security labs, ensuring high accuracy and compliance with global standards like ISO/IEC 30107-3.
By analyzing involuntary facial movements, eye blinks, and other micro-expressions, certified liveness detection systems can accurately differentiate between a live person and a fraudulent representation. This technology plays a vital role in preventing identity theft in remote onboarding, digital banking, and online KYC processes.
What is Voice Verification?
Voice verification, also known as voice biometrics, uses the unique vocal characteristics of an individual to verify their identity. Every person has a distinct voice pattern based on their vocal tract shape, pitch, accent, and speech rhythm. Voice verification systems capture and analyze these features to create a secure voiceprint, which is then matched during future authentications.
This method is non-invasive and ideal for hands-free verification, making it especially valuable in call centers, telecom, and mobile banking applications.
Why Combine Certified Liveness Detection and Voice Verification?
Combining liveness detection with voice verification adds a powerful layer of security to biometric authentication. While liveness detection confirms the presence of a real person, voice biometrics ensure that the person is indeed who they claim to be. This dual-layered system minimizes the risk of impersonation, deepfake attacks, and synthetic identity fraud.
For industries like finance, healthcare, and e-commerce, where identity assurance is paramount, this combination provides real-time, secure, and seamless user verification—boosting both compliance and customer trust.
Benefits of Using These Systems
-
✅ Enhanced Security against spoofing and deepfake threats
-
✅ Frictionless User Experience with quick and contactless authentication
-
✅ Regulatory Compliance with KYC, AML, and GDPR norms
-
✅ Scalability for remote onboarding and high-volume environments
-
✅ Reduced Fraud Risk in digital transactions and access controls
Conclusion
Certified liveness detection and voice verification systems are revolutionizing digital identity verification. As businesses continue to embrace remote operations and digital transformation, adopting these next-gen technologies ensures a safer and more reliable verification framework—setting new benchmarks for security, user experience, and compliance.
- Questions and Answers
- Opinion
- Motivational and Inspiring Story
- Technology
- Live and Let live
- Focus
- Geopolitics
- Military-Arms/Equipment
- Sécurité
- Economy
- Beasts of Nations
- Machine Tools-The “Mother Industry”
- Art
- Causes
- Crafts
- Dance
- Drinks
- Film/Movie
- Fitness
- Food
- Jeux
- Gardening
- Health
- Domicile
- Literature
- Music
- Networking
- Autre
- Party
- Religion
- Shopping
- Sports
- Theater
- Health and Wellness
- News
- Culture

