Kevin Mathew is an IT professional specializing in Customer Identity and Access Management (CIAM). With extensive experience in enhancing digital security and user experience, he drives innovation and efficiency in identity management solutions.
-
297 Записей
-
109 Фото
-
0 Видео
-
28/04/1995
-
Читают 0 человек
Недавние обновления
-
Understanding Digital Certificates: A Key to Web Security
Digital Certificates play a crucial role in establishing trust and ensuring secure communication over the internet. They help verify the identity of websites and encrypt data exchanges to protect sensitive information. In this guide, we explore what Digital Certificates are, how they work, and why they are essential for web security. Whether you're a developer or a security-conscious user, understanding Digital Certificates is key to staying protected in today’s digital landscape.
More Info - https://www.loginradius.com/blog/identity/what-are-digital-certificatesUnderstanding Digital Certificates: A Key to Web Security Digital Certificates play a crucial role in establishing trust and ensuring secure communication over the internet. They help verify the identity of websites and encrypt data exchanges to protect sensitive information. In this guide, we explore what Digital Certificates are, how they work, and why they are essential for web security. Whether you're a developer or a security-conscious user, understanding Digital Certificates is key to staying protected in today’s digital landscape. More Info - https://www.loginradius.com/blog/identity/what-are-digital-certificates WWW.LOGINRADIUS.COMWhat Are Digital Certificates and Why They MatterLearn what a digital certificate is, how it works, types, use cases, and how it builds trust in secure communication and identity verification.0 Комментарии 0 Поделились 503 Просмотры 0 предпросмотрВойдите, чтобы отмечать, делиться и комментировать!
WWW.LOGINRADIUS.COMWhat Are Digital Certificates and Why They MatterLearn what a digital certificate is, how it works, types, use cases, and how it builds trust in secure communication and identity verification.0 Комментарии 0 Поделились 503 Просмотры 0 предпросмотрВойдите, чтобы отмечать, делиться и комментировать! -
The Key Differences in B2B and B2C Authentication
Understanding the key differences in B2B vs B2C Authentication is essential for building secure and user-friendly access systems. While B2C focuses on individual users with simple login flows like social sign-ins, B2B authentication involves managing organizational hierarchies, role-based access, and multi-tenant structures. This guide highlights how authentication protocols, onboarding processes, access controls, and branding vary significantly between the two models - helping businesses choose the right identity approach for their target audience and operational needs.
More Info - https://www.loginradius.com/blog/identity/b2b-vs-b2c-authenticationThe Key Differences in B2B and B2C Authentication Understanding the key differences in B2B vs B2C Authentication is essential for building secure and user-friendly access systems. While B2C focuses on individual users with simple login flows like social sign-ins, B2B authentication involves managing organizational hierarchies, role-based access, and multi-tenant structures. This guide highlights how authentication protocols, onboarding processes, access controls, and branding vary significantly between the two models - helping businesses choose the right identity approach for their target audience and operational needs. More Info - https://www.loginradius.com/blog/identity/b2b-vs-b2c-authentication WWW.LOGINRADIUS.COMB2B vs B2C Authentication: Secure Partner & Consumer AccessExplore B2B vs B2C authentication differences, challenges, & best practices. Learn how Partner IAM secures APIs, users & workflows with LoginRadius.0 Комментарии 0 Поделились 437 Просмотры 0 предпросмотр
WWW.LOGINRADIUS.COMB2B vs B2C Authentication: Secure Partner & Consumer AccessExplore B2B vs B2C authentication differences, challenges, & best practices. Learn how Partner IAM secures APIs, users & workflows with LoginRadius.0 Комментарии 0 Поделились 437 Просмотры 0 предпросмотр -
Best Practices for Implementing B2B Identity and Access Management
Implementing B2B IAM best practices is essential for securely managing partner and third-party access to enterprise systems. This involves designing scalable identity architectures, enforcing role-based access control, and integrating with existing IT infrastructure. Strong authentication, audit trails, and lifecycle management ensure secure, compliant, and efficient identity handling. By following B2B IAM best practices, organizations can strengthen trust, enhance security, and improve collaboration with external partners while minimizing the risk of unauthorized access and data breaches in business-to-business environments.
More Info - https://www.loginradius.com/blog/identity/b2b-iam-best-practicesBest Practices for Implementing B2B Identity and Access Management Implementing B2B IAM best practices is essential for securely managing partner and third-party access to enterprise systems. This involves designing scalable identity architectures, enforcing role-based access control, and integrating with existing IT infrastructure. Strong authentication, audit trails, and lifecycle management ensure secure, compliant, and efficient identity handling. By following B2B IAM best practices, organizations can strengthen trust, enhance security, and improve collaboration with external partners while minimizing the risk of unauthorized access and data breaches in business-to-business environments. More Info - https://www.loginradius.com/blog/identity/b2b-iam-best-practices WWW.LOGINRADIUS.COMDelegated Administration in Partner IAM: Best PracticesDiscover Partner IAM best practices with delegated access control, B2B identity management, and how LoginRadius supports secure delegation.0 Комментарии 0 Поделились 1Кб Просмотры 0 предпросмотр
WWW.LOGINRADIUS.COMDelegated Administration in Partner IAM: Best PracticesDiscover Partner IAM best practices with delegated access control, B2B identity management, and how LoginRadius supports secure delegation.0 Комментарии 0 Поделились 1Кб Просмотры 0 предпросмотр -
The Role of User Authentication in Digital Security
User Authentication plays a vital role in digital security by ensuring that only authorized users gain access to sensitive systems and data. It verifies identities using methods like passwords, biometrics, or multi-factor authentication to prevent unauthorized access. As cyber threats continue to rise, robust User Authentication helps organizations protect confidential information, maintain trust, and comply with security standards. This foundational layer of defense is essential for securing digital platforms, applications, and networks against identity theft and data breaches.
More Info - https://www.loginradius.com/blog/identity/what-is-user-authenticationThe Role of User Authentication in Digital Security User Authentication plays a vital role in digital security by ensuring that only authorized users gain access to sensitive systems and data. It verifies identities using methods like passwords, biometrics, or multi-factor authentication to prevent unauthorized access. As cyber threats continue to rise, robust User Authentication helps organizations protect confidential information, maintain trust, and comply with security standards. This foundational layer of defense is essential for securing digital platforms, applications, and networks against identity theft and data breaches. More Info - https://www.loginradius.com/blog/identity/what-is-user-authentication WWW.LOGINRADIUS.COMWhat is User Authentication and Why Does It MatterLearn what user authentication is, how it works, why it’s important, and the best practices to build secure, user-friendly login experiences.0 Комментарии 0 Поделились 1Кб Просмотры 0 предпросмотр
WWW.LOGINRADIUS.COMWhat is User Authentication and Why Does It MatterLearn what user authentication is, how it works, why it’s important, and the best practices to build secure, user-friendly login experiences.0 Комментарии 0 Поделились 1Кб Просмотры 0 предпросмотр -
How Partner IAM Works: A Practical Guide
Partner IAM helps businesses securely manage access for external partners like vendors and affiliates. "How Partner IAM Works: A Practical Guide" explains the core components, including authentication, role-based access, and identity federation. The guide provides real-world examples and best practices to streamline onboarding, ensure data protection, and maintain control over third-party access. Whether you're new to Partner IAM or looking to optimize your current setup, this guide offers practical insights to enhance security and collaboration with external users.
More Info - https://www.loginradius.com/blog/identity/what-is-partner-iamHow Partner IAM Works: A Practical Guide Partner IAM helps businesses securely manage access for external partners like vendors and affiliates. "How Partner IAM Works: A Practical Guide" explains the core components, including authentication, role-based access, and identity federation. The guide provides real-world examples and best practices to streamline onboarding, ensure data protection, and maintain control over third-party access. Whether you're new to Partner IAM or looking to optimize your current setup, this guide offers practical insights to enhance security and collaboration with external users. More Info - https://www.loginradius.com/blog/identity/what-is-partner-iam0 Комментарии 0 Поделились 789 Просмотры 0 предпросмотр -
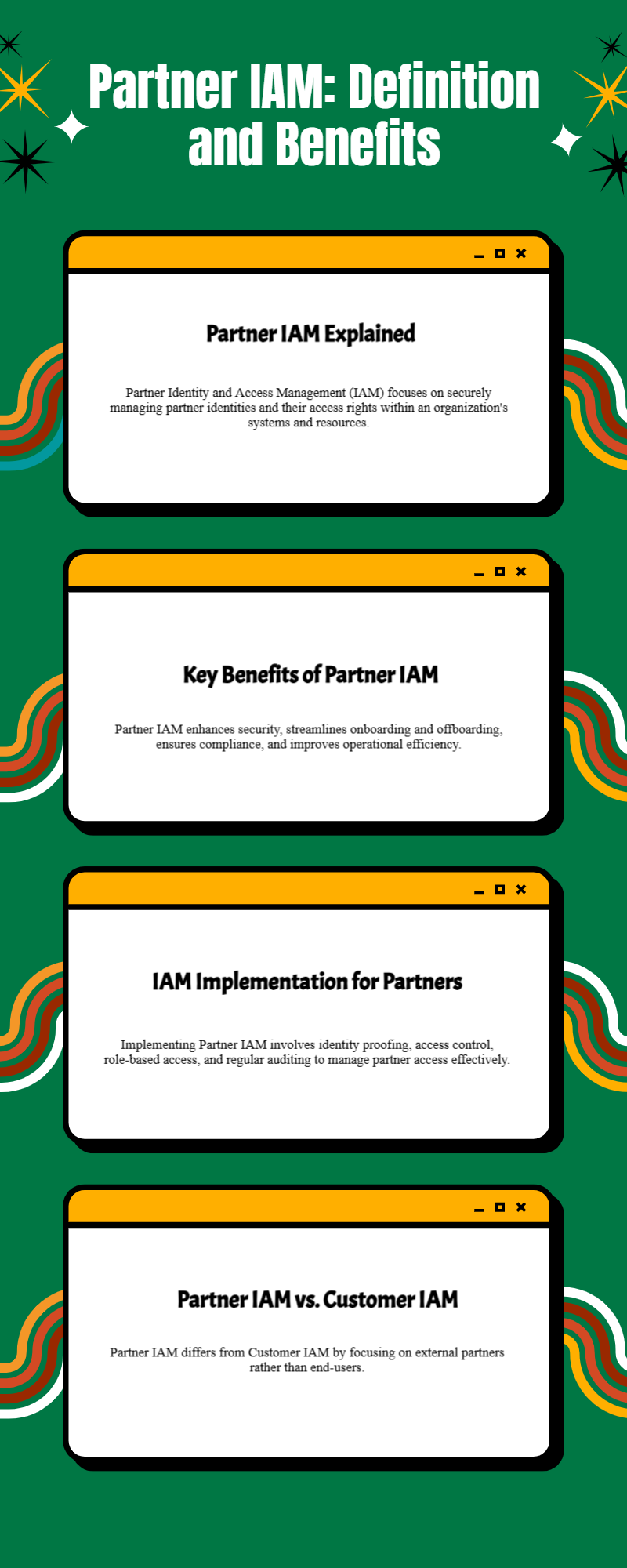
Understanding Partner IAM: A Complete Overview
Partner IAM (Identity and Access Management) is a solution designed to manage and secure access for external business partners such as vendors, affiliates, or resellers. In "Understanding Partner IAM: A Complete Overview," you’ll learn how Partner IAM streamlines onboarding, enhances security, and ensures controlled access to sensitive resources. This guide covers the benefits, key features, and best practices for implementing Partner IAM to build trust and improve collaboration with external users while maintaining enterprise-grade identity security.
More Info - https://www.loginradius.com/blog/identity/what-is-partner-iamUnderstanding Partner IAM: A Complete Overview Partner IAM (Identity and Access Management) is a solution designed to manage and secure access for external business partners such as vendors, affiliates, or resellers. In "Understanding Partner IAM: A Complete Overview," you’ll learn how Partner IAM streamlines onboarding, enhances security, and ensures controlled access to sensitive resources. This guide covers the benefits, key features, and best practices for implementing Partner IAM to build trust and improve collaboration with external users while maintaining enterprise-grade identity security. More Info - https://www.loginradius.com/blog/identity/what-is-partner-iam WWW.LOGINRADIUS.COMWhat is Partner IAM? Secure B2B Access ExplainedLearn how Partner/ B2B IAM enables secure, scalable access for vendors, agencies, and partners with SSO, JIT provisioning, and granular role management.0 Комментарии 0 Поделились 1Кб Просмотры 0 предпросмотр
WWW.LOGINRADIUS.COMWhat is Partner IAM? Secure B2B Access ExplainedLearn how Partner/ B2B IAM enables secure, scalable access for vendors, agencies, and partners with SSO, JIT provisioning, and granular role management.0 Комментарии 0 Поделились 1Кб Просмотры 0 предпросмотр -
How Biometric Authentication Is Replacing Traditional Logins
Biometric Authentication is rapidly transforming how we access digital services by replacing traditional logins like passwords and PINs. Leveraging unique physical traits such as fingerprints, facial recognition, or iris scans, biometric authentication offers a more secure and user-friendly alternative. It minimizes the risks of password breaches, phishing, and identity theft. As more organizations adopt this technology, the future of secure and seamless access lies in biometrics. Discover how it's redefining authentication in the digital age.
More Info - https://www.loginradius.com/blog/identity/what-is-biometric-authenticationHow Biometric Authentication Is Replacing Traditional Logins Biometric Authentication is rapidly transforming how we access digital services by replacing traditional logins like passwords and PINs. Leveraging unique physical traits such as fingerprints, facial recognition, or iris scans, biometric authentication offers a more secure and user-friendly alternative. It minimizes the risks of password breaches, phishing, and identity theft. As more organizations adopt this technology, the future of secure and seamless access lies in biometrics. Discover how it's redefining authentication in the digital age. More Info - https://www.loginradius.com/blog/identity/what-is-biometric-authentication WWW.LOGINRADIUS.COMBiometric Login Explained: Methods, Benefits & RisksExplore what biometric authentication is, how it secures identity with fingerprints or face scans, and why it’s replacing passwords in modern apps.0 Комментарии 0 Поделились 1Кб Просмотры 0 предпросмотр
WWW.LOGINRADIUS.COMBiometric Login Explained: Methods, Benefits & RisksExplore what biometric authentication is, how it secures identity with fingerprints or face scans, and why it’s replacing passwords in modern apps.0 Комментарии 0 Поделились 1Кб Просмотры 0 предпросмотр -
Passkeys vs Passwords: Which One Secures You Better?
Passkeys vs Passwords is an ongoing debate in the world of digital security. As cyber threats evolve, users need safer, smarter authentication methods. This article compares passkeys - biometric or device-based login methods - with traditional passwords to determine which offers better protection. Discover the strengths and weaknesses of each, how they function, and why tech leaders are shifting toward passwordless solutions. If you're looking to improve your online security, understanding the difference between passkeys vs passwords is essential for making informed choices.
More Info - https://www.loginradius.com/blog/identity/passkeys-vs-passwordsPasskeys vs Passwords: Which One Secures You Better? Passkeys vs Passwords is an ongoing debate in the world of digital security. As cyber threats evolve, users need safer, smarter authentication methods. This article compares passkeys - biometric or device-based login methods - with traditional passwords to determine which offers better protection. Discover the strengths and weaknesses of each, how they function, and why tech leaders are shifting toward passwordless solutions. If you're looking to improve your online security, understanding the difference between passkeys vs passwords is essential for making informed choices. More Info - https://www.loginradius.com/blog/identity/passkeys-vs-passwords WWW.LOGINRADIUS.COMPasskeys vs Passwords: Enhancing Security with Password ManagersDiscover the advantages of combining passkeys and passwords using password managers for optimal digital security and user convenience.0 Комментарии 0 Поделились 1Кб Просмотры 0 предпросмотр
WWW.LOGINRADIUS.COMPasskeys vs Passwords: Enhancing Security with Password ManagersDiscover the advantages of combining passkeys and passwords using password managers for optimal digital security and user convenience.0 Комментарии 0 Поделились 1Кб Просмотры 0 предпросмотр -
How Local Data Residency Enhances Customer Trust and Sales
Regional data storage plays a critical role in building customer trust and driving sales. This blog explores how storing user data within specific geographic regions helps businesses comply with local regulations, improve data security, and reassure customers that their information is handled responsibly. By prioritizing local data residency, companies not only meet compliance requirements but also enhance transparency and credibility - ultimately leading to higher customer confidence, stronger brand loyalty, and improved conversion rates across markets that value data privacy.
More Info - https://www.loginradius.com/blog/identity/regional-storage-boost-trust-conversionHow Local Data Residency Enhances Customer Trust and Sales Regional data storage plays a critical role in building customer trust and driving sales. This blog explores how storing user data within specific geographic regions helps businesses comply with local regulations, improve data security, and reassure customers that their information is handled responsibly. By prioritizing local data residency, companies not only meet compliance requirements but also enhance transparency and credibility - ultimately leading to higher customer confidence, stronger brand loyalty, and improved conversion rates across markets that value data privacy. More Info - https://www.loginradius.com/blog/identity/regional-storage-boost-trust-conversion WWW.LOGINRADIUS.COMHow Location-Based Regional Storage Boosts eCommerce SalesDiscover how regional data storage helps retailers meet compliance, build trust, protect customer data, and improve checkout conversions.0 Комментарии 0 Поделились 1Кб Просмотры 0 предпросмотр
WWW.LOGINRADIUS.COMHow Location-Based Regional Storage Boosts eCommerce SalesDiscover how regional data storage helps retailers meet compliance, build trust, protect customer data, and improve checkout conversions.0 Комментарии 0 Поделились 1Кб Просмотры 0 предпросмотр -
How AI Is Transforming the Future of Cybersecurity
AI in cybersecurity is revolutionizing how we detect, prevent, and respond to cyber threats. In this blog, we explore how artificial intelligence is transforming the future of cybersecurity by enabling faster threat detection, predictive analytics, and automated incident response. From identifying unusual behavior to adapting to evolving attack patterns, AI empowers security teams with advanced tools for smarter defense. Discover how AI-driven solutions are reshaping cybersecurity and preparing organizations to face increasingly sophisticated digital threats with confidence.
More Info - https://www.loginradius.com/blog/identity/ai-and-cybersecurityHow AI Is Transforming the Future of Cybersecurity AI in cybersecurity is revolutionizing how we detect, prevent, and respond to cyber threats. In this blog, we explore how artificial intelligence is transforming the future of cybersecurity by enabling faster threat detection, predictive analytics, and automated incident response. From identifying unusual behavior to adapting to evolving attack patterns, AI empowers security teams with advanced tools for smarter defense. Discover how AI-driven solutions are reshaping cybersecurity and preparing organizations to face increasingly sophisticated digital threats with confidence. More Info - https://www.loginradius.com/blog/identity/ai-and-cybersecurity WWW.LOGINRADIUS.COMAI in Cybersecurity: Innovations, Benefits & Future TrendsExplore the impact of AI in cybersecurity, from threat detection to adaptive authentication. Learn how AI improves data protection across industries.0 Комментарии 0 Поделились 2Кб Просмотры 0 предпросмотр
WWW.LOGINRADIUS.COMAI in Cybersecurity: Innovations, Benefits & Future TrendsExplore the impact of AI in cybersecurity, from threat detection to adaptive authentication. Learn how AI improves data protection across industries.0 Комментарии 0 Поделились 2Кб Просмотры 0 предпросмотр -
PINs vs Passwords: What’s the Better Choice for Security?
PINs vs Passwords is a key debate in the world of digital security. This blog explores which method offers better protection for your devices and accounts. While passwords have long been the standard, PINs - especially when tied to a specific device - can offer stronger, localized security. We’ll break down the pros, cons, and ideal use cases for both methods to help you choose the safest option for your needs. Discover which authentication method truly keeps your information secure.
More Info - https://www.loginradius.com/blog/identity/pin-vs-passwordsPINs vs Passwords: What’s the Better Choice for Security? PINs vs Passwords is a key debate in the world of digital security. This blog explores which method offers better protection for your devices and accounts. While passwords have long been the standard, PINs - especially when tied to a specific device - can offer stronger, localized security. We’ll break down the pros, cons, and ideal use cases for both methods to help you choose the safest option for your needs. Discover which authentication method truly keeps your information secure. More Info - https://www.loginradius.com/blog/identity/pin-vs-passwords WWW.LOGINRADIUS.COMPINs vs Passwords: Which is More Secure?Discover the difference between PIN vs password, and learn how to enhance your login security with secure PINs and strong passwords.0 Комментарии 0 Поделились 845 Просмотры 0 предпросмотр
WWW.LOGINRADIUS.COMPINs vs Passwords: Which is More Secure?Discover the difference between PIN vs password, and learn how to enhance your login security with secure PINs and strong passwords.0 Комментарии 0 Поделились 845 Просмотры 0 предпросмотр -
How TOTP Keeps Your Accounts Safe
TOTP Authentication, or Time-Based One-Time Password, is a powerful method to protect your online accounts. It generates a unique code every 30 seconds, ensuring that even if someone steals your password, they can't log in without the current code. This added layer of security helps prevent unauthorized access and is widely used in apps like Google Authenticator. Understanding how TOTP keeps your accounts safe is key to strengthening your overall cybersecurity and protecting sensitive information.
More Info - https://www.loginradius.com/blog/engineering/what-is-totp-authenticationHow TOTP Keeps Your Accounts Safe TOTP Authentication, or Time-Based One-Time Password, is a powerful method to protect your online accounts. It generates a unique code every 30 seconds, ensuring that even if someone steals your password, they can't log in without the current code. This added layer of security helps prevent unauthorized access and is widely used in apps like Google Authenticator. Understanding how TOTP keeps your accounts safe is key to strengthening your overall cybersecurity and protecting sensitive information. More Info - https://www.loginradius.com/blog/engineering/what-is-totp-authentication WWW.LOGINRADIUS.COMWhat is TOTP? Time-Based One-Time Password ExplainedDiscover what a time-based one-time password (TOTP) is, how it works, and why it's a trusted, offline-ready method for secure multi-factor authentication.0 Комментарии 0 Поделились 862 Просмотры 0 предпросмотр
WWW.LOGINRADIUS.COMWhat is TOTP? Time-Based One-Time Password ExplainedDiscover what a time-based one-time password (TOTP) is, how it works, and why it's a trusted, offline-ready method for secure multi-factor authentication.0 Комментарии 0 Поделились 862 Просмотры 0 предпросмотр -
Passkeys vs Passwords: Which Is Safer
Passkeys vs Passwords is a hot topic in modern cybersecurity. While passwords have long been the standard, they’re often weak, reused, and vulnerable to attacks. Passkeys offer a safer alternative by using cryptographic authentication, eliminating the need to remember complex strings. This guide explores the key differences in security, usability, and future adoption. If you’re looking to upgrade your login methods, understanding Passkeys vs Passwords is essential for making smarter, more secure authentication choices.
More Info - https://www.loginradius.com/blog/identity/passkeys-vs-passwordsPasskeys vs Passwords: Which Is Safer Passkeys vs Passwords is a hot topic in modern cybersecurity. While passwords have long been the standard, they’re often weak, reused, and vulnerable to attacks. Passkeys offer a safer alternative by using cryptographic authentication, eliminating the need to remember complex strings. This guide explores the key differences in security, usability, and future adoption. If you’re looking to upgrade your login methods, understanding Passkeys vs Passwords is essential for making smarter, more secure authentication choices. More Info - https://www.loginradius.com/blog/identity/passkeys-vs-passwords WWW.LOGINRADIUS.COMPasskeys vs Passwords: Enhancing Security with Password ManagersDiscover the advantages of combining passkeys and passwords using password managers for optimal digital security and user convenience.0 Комментарии 0 Поделились 1Кб Просмотры 0 предпросмотр
WWW.LOGINRADIUS.COMPasskeys vs Passwords: Enhancing Security with Password ManagersDiscover the advantages of combining passkeys and passwords using password managers for optimal digital security and user convenience.0 Комментарии 0 Поделились 1Кб Просмотры 0 предпросмотр -
Why Canadian Data Centers Excel in Privacy
Canadian data centers excel in privacy due to the country’s strong data protection laws, including PIPEDA, and a commitment to regulatory compliance. With strict security standards, data sovereignty policies, and advanced infrastructure, Canada offers a reliable environment for privacy-first hosting. Businesses worldwide trust Canadian data centers to safeguard sensitive information.
More Info - https://www.loginradius.com/blog/identity/canada-leads-global-data-hostingWhy Canadian Data Centers Excel in Privacy Canadian data centers excel in privacy due to the country’s strong data protection laws, including PIPEDA, and a commitment to regulatory compliance. With strict security standards, data sovereignty policies, and advanced infrastructure, Canada offers a reliable environment for privacy-first hosting. Businesses worldwide trust Canadian data centers to safeguard sensitive information. More Info - https://www.loginradius.com/blog/identity/canada-leads-global-data-hosting WWW.LOGINRADIUS.COMWhy Canada Is a Privacy-First Data Hosting LeaderFind out why global businesses are trusting Canada for its strong privacy laws, stable government, and strong data control.0 Комментарии 0 Поделились 1Кб Просмотры 0 предпросмотр
WWW.LOGINRADIUS.COMWhy Canada Is a Privacy-First Data Hosting LeaderFind out why global businesses are trusting Canada for its strong privacy laws, stable government, and strong data control.0 Комментарии 0 Поделились 1Кб Просмотры 0 предпросмотр -
How to Authenticate Users Securely in 2025
Learn how to authenticate users securely in 2025 using advanced authentication methods like biometrics, passkeys, and multi-factor authentication (MFA). This guide covers the latest trends in user verification, helping developers and businesses choose the right techniques to enhance security and user experience. From eliminating passwords to adopting adaptive authentication, stay ahead with best practices that safeguard digital access while keeping usability in focus.
More Info - https://www.loginradius.com/blog/identity/best-way-to-authenticate-usersHow to Authenticate Users Securely in 2025 Learn how to authenticate users securely in 2025 using advanced authentication methods like biometrics, passkeys, and multi-factor authentication (MFA). This guide covers the latest trends in user verification, helping developers and businesses choose the right techniques to enhance security and user experience. From eliminating passwords to adopting adaptive authentication, stay ahead with best practices that safeguard digital access while keeping usability in focus. More Info - https://www.loginradius.com/blog/identity/best-way-to-authenticate-users WWW.LOGINRADIUS.COMUser Authentication Methods for Secure & Seamless LoginExplore the top user authentication methods—MFA, passkeys, biometrics—and how to choose the safest login strategy for your organization.0 Комментарии 0 Поделились 1Кб Просмотры 0 предпросмотр
WWW.LOGINRADIUS.COMUser Authentication Methods for Secure & Seamless LoginExplore the top user authentication methods—MFA, passkeys, biometrics—and how to choose the safest login strategy for your organization.0 Комментарии 0 Поделились 1Кб Просмотры 0 предпросмотр -
A Beginner’s Guide to Choosing a Strong Password
Choosing a strong password is essential for protecting your online accounts from cyber threats. This beginner’s guide walks you through the basics of creating secure passwords that are hard to guess but easy to remember. Learn tips like using a mix of characters, avoiding personal information, and using passphrases. You'll also discover tools like password managers that make managing multiple strong passwords simple. Start building safer digital habits today with this easy-to-follow guide on crafting the perfect strong password.
More Info - https://www.loginradius.com/blog/identity/how-to-choose-a-strong-passwordA Beginner’s Guide to Choosing a Strong Password Choosing a strong password is essential for protecting your online accounts from cyber threats. This beginner’s guide walks you through the basics of creating secure passwords that are hard to guess but easy to remember. Learn tips like using a mix of characters, avoiding personal information, and using passphrases. You'll also discover tools like password managers that make managing multiple strong passwords simple. Start building safer digital habits today with this easy-to-follow guide on crafting the perfect strong password. More Info - https://www.loginradius.com/blog/identity/how-to-choose-a-strong-password WWW.LOGINRADIUS.COMHow to Choose a Strong Password- A Quick GuideWith billions of passwords leaked, weak credentials are no longer just risky—they're dangerous. Learn how to build strong, unique passwords that can resist modern cyberattacks. This guide breaks down techniques, tools, and policy tips to help you stay secure.0 Комментарии 0 Поделились 1Кб Просмотры 0 предпросмотр
WWW.LOGINRADIUS.COMHow to Choose a Strong Password- A Quick GuideWith billions of passwords leaked, weak credentials are no longer just risky—they're dangerous. Learn how to build strong, unique passwords that can resist modern cyberattacks. This guide breaks down techniques, tools, and policy tips to help you stay secure.0 Комментарии 0 Поделились 1Кб Просмотры 0 предпросмотр -
Comprehensive Guide to Device-Based Authentication
Device authentication methods play a critical role in ensuring secure access to digital systems by verifying the legitimacy of the user's device. This Comprehensive Guide to Device-Based Authentication explores various techniques such as device certificates, hardware tokens, and biometric-enabled devices. Learn how businesses can strengthen security, reduce fraud, and improve user experience with the right device authentication methods. Whether you're new to identity security or refining your existing strategy, this guide offers practical insights for implementing effective device-based authentication.
More Info - https://www.loginradius.com/blog/identity/device-authentication-methodsComprehensive Guide to Device-Based Authentication Device authentication methods play a critical role in ensuring secure access to digital systems by verifying the legitimacy of the user's device. This Comprehensive Guide to Device-Based Authentication explores various techniques such as device certificates, hardware tokens, and biometric-enabled devices. Learn how businesses can strengthen security, reduce fraud, and improve user experience with the right device authentication methods. Whether you're new to identity security or refining your existing strategy, this guide offers practical insights for implementing effective device-based authentication. More Info - https://www.loginradius.com/blog/identity/device-authentication-methods WWW.LOGINRADIUS.COMA Complete Guide to Device Authentication MethodsExplore how device authentication goes beyond passwords to verify not just users, but the devices they use. From biometrics and tokens to machine-to-machine (M2M) authorization, learn the methods that help secure modern digital ecosystems against spoofing, theft, and misuse.0 Комментарии 0 Поделились 930 Просмотры 0 предпросмотр
WWW.LOGINRADIUS.COMA Complete Guide to Device Authentication MethodsExplore how device authentication goes beyond passwords to verify not just users, but the devices they use. From biometrics and tokens to machine-to-machine (M2M) authorization, learn the methods that help secure modern digital ecosystems against spoofing, theft, and misuse.0 Комментарии 0 Поделились 930 Просмотры 0 предпросмотр -
How to Choose the Right Authentication Method for Your Business
Choosing the right Authentication Methods is essential for ensuring secure access and protecting sensitive business data. This guide explores the most common authentication types—such as passwords, biometrics, and multi-factor authentication - and helps you evaluate which is best suited for your organization’s size, risk level, and user needs. Whether you're a startup or an enterprise, understanding the pros and cons of various Authentication Methods can help you make informed decisions that balance usability with security. Discover the best approach for your business today.
More Info - https://www.loginradius.com/blog/identity/how-to-choose-authenticationHow to Choose the Right Authentication Method for Your Business Choosing the right Authentication Methods is essential for ensuring secure access and protecting sensitive business data. This guide explores the most common authentication types—such as passwords, biometrics, and multi-factor authentication - and helps you evaluate which is best suited for your organization’s size, risk level, and user needs. Whether you're a startup or an enterprise, understanding the pros and cons of various Authentication Methods can help you make informed decisions that balance usability with security. Discover the best approach for your business today. More Info - https://www.loginradius.com/blog/identity/how-to-choose-authentication WWW.LOGINRADIUS.COMGuide to Authentication Methods & Choosing the Right OneChoosing the right authentication method can impact security, compliance, and user experience. This blog breaks down various authentication types and factors to consider in 2025 and also portrays how LoginRadius makes secure, scalable implementation easy.0 Комментарии 0 Поделились 939 Просмотры 0 предпросмотр
WWW.LOGINRADIUS.COMGuide to Authentication Methods & Choosing the Right OneChoosing the right authentication method can impact security, compliance, and user experience. This blog breaks down various authentication types and factors to consider in 2025 and also portrays how LoginRadius makes secure, scalable implementation easy.0 Комментарии 0 Поделились 939 Просмотры 0 предпросмотр -
What Is OTP in Authentication? A Comprehensive Guide
One-time password (OTP) is a powerful security tool used to verify user identity during authentication. In this comprehensive guide, we explore what a one time password is, how it works, and why it’s widely used in login and transaction verification. OTPs are temporary codes that add an extra layer of security, helping prevent unauthorized access. Whether sent via SMS, email, or an app, a one time password ensures secure, time-sensitive user verification in today's digital world.
More Info - https://www.loginradius.com/blog/identity/what-is-one-time-passwordWhat Is OTP in Authentication? A Comprehensive Guide One-time password (OTP) is a powerful security tool used to verify user identity during authentication. In this comprehensive guide, we explore what a one time password is, how it works, and why it’s widely used in login and transaction verification. OTPs are temporary codes that add an extra layer of security, helping prevent unauthorized access. Whether sent via SMS, email, or an app, a one time password ensures secure, time-sensitive user verification in today's digital world. More Info - https://www.loginradius.com/blog/identity/what-is-one-time-password WWW.LOGINRADIUS.COMWhat is a One-Time Password (OTP) ? – A Complete GuideDiscover how One-Time Passwords (OTPs) enhance digital security by preventing breaches, phishing, and fraud. Learn how OTPs work, their types, use cases across industries, and how to implement them securely. From TOTP and HOTP to real-world case studies, this guide covers everything about OTP authentication in one place.0 Комментарии 0 Поделились 609 Просмотры 0 предпросмотр
WWW.LOGINRADIUS.COMWhat is a One-Time Password (OTP) ? – A Complete GuideDiscover how One-Time Passwords (OTPs) enhance digital security by preventing breaches, phishing, and fraud. Learn how OTPs work, their types, use cases across industries, and how to implement them securely. From TOTP and HOTP to real-world case studies, this guide covers everything about OTP authentication in one place.0 Комментарии 0 Поделились 609 Просмотры 0 предпросмотр -
Exploring the Benefits of TOTP for User Authentication
Time-Based One-Time Passwords (TOTP) offer a secure way to verify users beyond traditional login credentials. In this article, we explore the key advantages of TOTP for user authentication, including enhanced protection against phishing, reduced reliance on SMS, and better control over access security. By generating short-lived codes tied to time and a shared secret, TOTP makes unauthorized access far more difficult. Learn why TOTP is a trusted method for strengthening authentication and securing digital identities across applications and platforms.
More Info - https://www.loginradius.com/blog/engineering/advantages-of-totpExploring the Benefits of TOTP for User Authentication Time-Based One-Time Passwords (TOTP) offer a secure way to verify users beyond traditional login credentials. In this article, we explore the key advantages of TOTP for user authentication, including enhanced protection against phishing, reduced reliance on SMS, and better control over access security. By generating short-lived codes tied to time and a shared secret, TOTP makes unauthorized access far more difficult. Learn why TOTP is a trusted method for strengthening authentication and securing digital identities across applications and platforms. More Info - https://www.loginradius.com/blog/engineering/advantages-of-totp WWW.LOGINRADIUS.COMAdvantages of Time-Based One-Time Passwords (TOTP)Discover how Time-Based One-Time Passwords (TOTP) bolster cybersecurity through dynamic, temporary authentication codes. Explore TOTP's advantages, including phishing resistance, offline functionality, and seamless integration. Implement TOTP effectively for secure, user-friendly authentication solutions.0 Комментарии 0 Поделились 1Кб Просмотры 0 предпросмотр
WWW.LOGINRADIUS.COMAdvantages of Time-Based One-Time Passwords (TOTP)Discover how Time-Based One-Time Passwords (TOTP) bolster cybersecurity through dynamic, temporary authentication codes. Explore TOTP's advantages, including phishing resistance, offline functionality, and seamless integration. Implement TOTP effectively for secure, user-friendly authentication solutions.0 Комментарии 0 Поделились 1Кб Просмотры 0 предпросмотр
Больше
Спонсоры