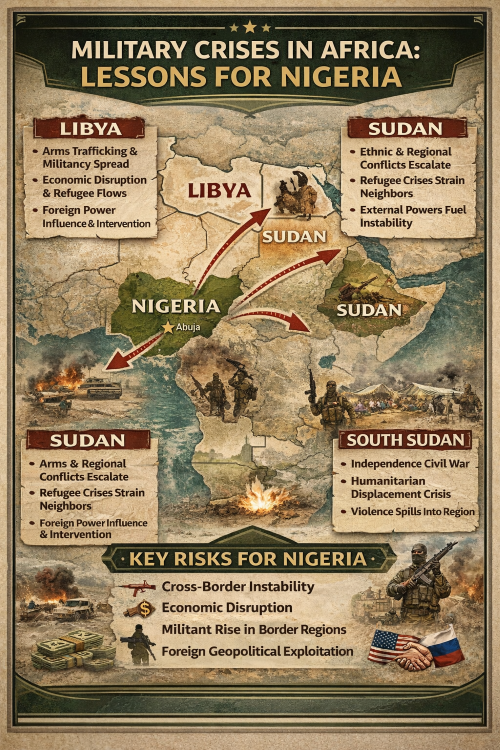
Nigeria as a Strategic Launchpad
Why Nigeria Is Uniquely Positioned as a Military and Logistical Hub in West Africa
Beyond Size—Toward Strategic Centrality
Nigeria’s importance in West Africa is often reduced to numbers: population size, GDP, oil production, or troop contributions to peacekeeping missions. While these factors matter, they do not fully explain why Nigeria repeatedly emerges—implicitly or explicitly—as a preferred military and logistical anchor for external powers operating in West Africa.
Nigeria’s true value lies not just in its scale, but in its geostrategic geometry. It sits at the intersection of coastal access, Sahelian depth, demographic mass, infrastructure density, and regional legitimacy. These attributes combine to make Nigeria not merely another partner state, but a strategic launchpad—a platform from which influence, logistics, and security operations can radiate across West Africa and into the Sahel.
1. Geographic Centrality: Nigeria as the Pivot State
Nigeria occupies a central hinge position in West Africa:
- It borders four countries directly (Benin, Niger, Chad, Cameroon)
- It lies between the Atlantic coast and the Sahel
- It straddles multiple ecological and security zones: coastal, forest, savannah, and semi-arid
This geography allows Nigeria to function as:
- A coastal gateway for maritime access
- A land bridge into the Sahel
- A buffer zone between fragile inland states and the Gulf of Guinea
From a military planning perspective, Nigeria enables multi-directional reach. Forces, supplies, intelligence assets, and communications based in Nigeria can support operations westward (Benin, Togo, Ghana), northward (Niger, Chad), eastward (Cameroon, Lake Chad Basin), and offshore (Gulf of Guinea).
No other West African country offers this combination of depth, access, and centrality.
2. Demographic and Human Capital Depth
With over 200 million people, Nigeria provides:
- A vast recruitment base
- A large pool of technical, engineering, and logistics personnel
- Indigenous language, cultural, and regional knowledge critical for operations
For external military actors, Nigeria offers something rare: scale without total dependency. Unlike smaller states, Nigeria can host or cooperate without appearing as a client state. This creates political cover for sustained engagement.
Additionally:
- Nigerian officers have extensive experience in multinational operations
- The country has produced generations of military leadership integrated into regional and global security networks
This human capital reduces the transaction cost of coordination and integration.
3. Infrastructure Density: Ports, Roads, Airfields, and Networks
Nigeria’s infrastructure—though uneven and often strained—is denser and more diversified than that of its neighbors.
Key assets include:
- Major seaports (Lagos, Port Harcourt, Onne)
- Multiple international airports with heavy-lift capability
- Extensive road networks linking coast to interior
- Telecommunications and energy infrastructure supporting command and control
From a logistical standpoint, Nigeria allows:
- Rapid importation of equipment
- Storage and redistribution of supplies
- Rotation of personnel
- Medical evacuation and sustainment operations
In contrast, Sahelian states often lack:
- Reliable ports
- Redundant airfields
- Secure supply corridors
This makes Nigeria the rear logistics base even when operations occur elsewhere.
4. Existing Military Capacity and Regional Legitimacy
Nigeria possesses the largest and most experienced military force in West Africa. While not without challenges, its armed forces have:
- Combat experience across multiple theaters
- Institutional familiarity with counterinsurgency and peacekeeping
- Command structures capable of coordinating multinational forces
Crucially, Nigeria’s leadership role in:
- ECOWAS
- ECOMOG
- African Union missions
provides regional legitimacy that external powers cannot generate independently.
Operating with Nigeria often appears more acceptable than operating over Nigeria.
5. Nigeria as the Anchor of ECOWAS Security Architecture
Nigeria is the de facto security backbone of ECOWAS.
- It contributes the majority of troops and funding
- It shapes regional security doctrine
- It provides political leadership during crises
This means that any external military coordination with ECOWAS implicitly passes through Nigeria—either formally or informally.
For external powers, Nigeria functions as:
- A gatekeeper state
- A legitimizing intermediary
- A bridge between national and regional frameworks
This role magnifies Nigeria’s strategic value far beyond its borders.
6. Maritime Significance: The Gulf of Guinea Factor
Nigeria anchors the Gulf of Guinea, one of the world’s most strategic maritime zones:
- Major energy shipping lanes
- Critical undersea communication cables
- High-volume commercial traffic
- Persistent piracy and maritime insecurity risks
Control, monitoring, or cooperation in Nigerian waters enables:
- Maritime domain awareness across the Gulf
- Protection of global trade routes
- Surveillance of offshore energy infrastructure
Any power concerned with maritime security in West Africa must engage Nigeria—not as an option, but as a necessity.
7. Security Spillover Dynamics: Nigeria as Containment Hub
Nigeria sits adjacent to multiple security fault lines:
- Lake Chad Basin insurgency
- Sahelian instability
- Cross-border banditry
- Maritime crime
Because threats spill into Nigeria rather than solely from it, external military cooperation can be framed as defensive and stabilizing, even when it enables regional reach.
This makes Nigeria an ideal containment hub:
- Threats are addressed before reaching coastal or global trade nodes
- Operations can be justified under mutual defense
8. Political Weight and Strategic Ambiguity
Nigeria maintains a tradition of strategic non-alignment rhetoric, even while cooperating with multiple global powers.
This ambiguity is valuable:
- It allows external powers to engage without forcing Nigeria into overt alliance blocs
- It enables Nigeria to host cooperation without formal basing agreements
- It reduces domestic backlash compared to smaller, more visibly dependent states
From a strategic perspective, Nigeria offers access without overt alignment—a highly prized condition in competitive geopolitical environments.
9. Why Nigeria, Not the Sahel, Becomes the Launchpad
Recent history shows that Sahelian states are:
- Politically volatile
- Resistant to prolonged foreign military presence
- Increasingly nationalist in response to perceived external control
Nigeria, by contrast:
- Retains institutional continuity
- Has stronger civilian-military structures
- Possesses diplomatic resilience
Thus, while operations may target the Sahel, Nigeria becomes the staging ground.
10. The Strategic Risk for Nigeria
This positioning is not cost-free.
Risks include:
- Becoming entangled in external power competition
- Internal backlash against perceived loss of sovereignty
- Being targeted by groups reacting to external presence
- Strategic overextension of Nigeria’s own security forces
The difference between leadership and leverage depends on Nigeria’s ability to set terms, not merely host cooperation.
Conclusion: Nigeria as Platform, Not Periphery
Nigeria’s role as a military and logistical hub is not accidental. It is the product of:
- Geographic centrality
- Demographic depth
- Infrastructure scale
- Military capacity
- Regional legitimacy
- Political weight
Together, these factors make Nigeria less a frontline battlefield and more a strategic platform—a launchpad from which security, influence, and power can be projected across West Africa.
The decisive question going forward is not whether Nigeria will be used as such a hub, but whether Nigeria will shape that role deliberately—or have it shaped for it.
In geopolitics, launchpads are never neutral. They are either instruments of agency or objects of positioning.