Is India’s infantry adequately equipped for next-generation battlefield challenges, from drones to cyberwarfare?
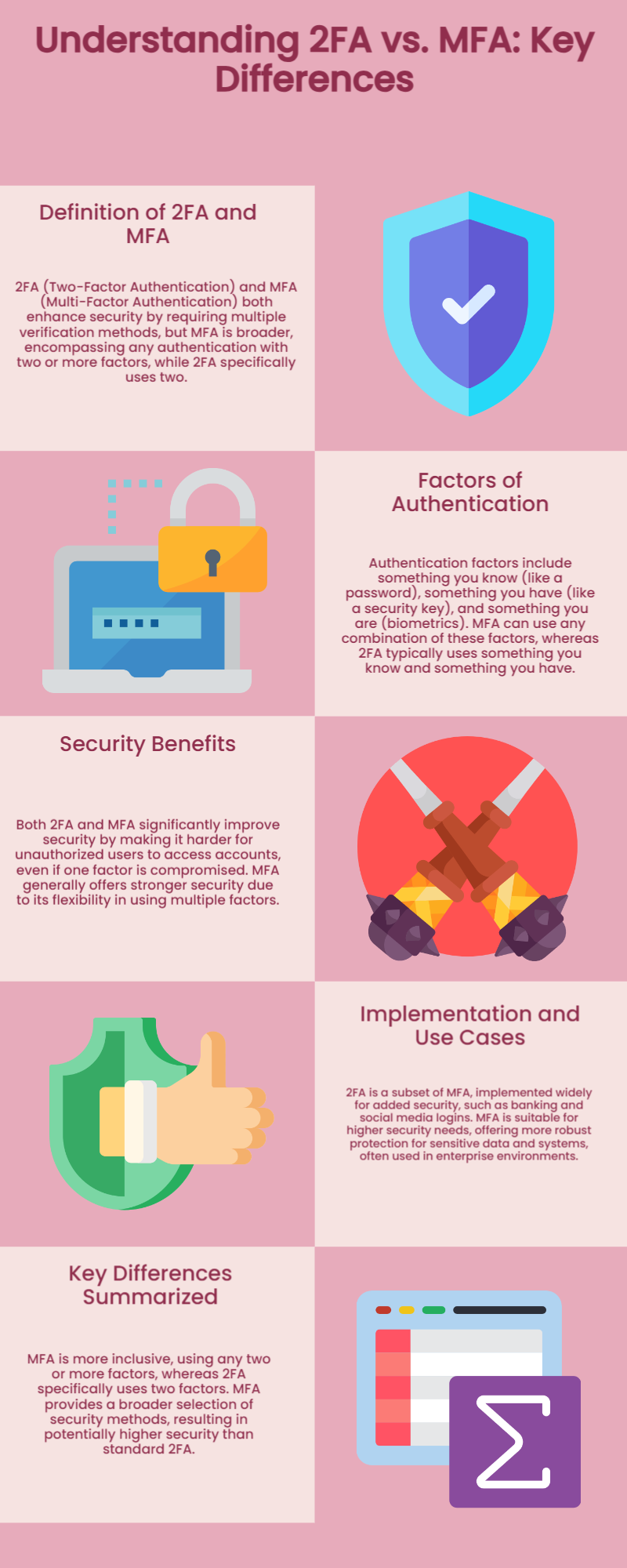
India's infantry is undergoing a significant transformation to meet the challenges of modern warfare, but its readiness is a mix of promising advancements and persistent gaps.
The military recognizes that the traditional "foot soldier" must evolve into a "technology-empowered warfighter" to be effective on a modern battlefield dominated by drones, cyber threats, and network-centric operations.
Modernization Efforts and Strengths
The Indian Army's Futuristic Infantry Soldier as a System (F-INSAS) program is at the heart of this modernization drive.
It's a comprehensive initiative that aims to upgrade every aspect of the soldier's gear, from firepower to survivability and digital integration.
Upgraded Firepower: The Indian Army has been phasing out its long-standing INSAS rifles, which were known for their reliability issues, in favor of modern assault rifles like the Sig Sauer 716 and the AK-203.
This is a significant step towards improving the soldier's primary weapon. Additionally, the infantry is being equipped with advanced anti-tank guided missiles, precision-guided munitions, and modern grenade launchers to enhance their ability to engage enemy fortifications and armored threats.
Enhanced Survivability: The push for indigenous Level 6 body armor, which provides enhanced ballistic protection without excessive weight, is a crucial step towards better protecting soldiers.
The Defence Research and Development Organisation (DRDO) is also exploring the use of exoskeletons to increase endurance and reduce the physical burden on soldiers in difficult terrains.
Counter-Drone Capabilities: India is actively developing and deploying counter-drone systems to protect its infantry from the growing threat of unmanned aerial vehicles (UAVs) and loitering munitions. The "Bhargavastra" system, developed by a private Indian company, is a notable example. It is a multi-layered, low-cost system designed to detect and neutralize drone swarms with micro-missiles and rockets.
Furthermore, every infantry battalion is being equipped with a dedicated drone platoon to enhance reconnaissance, target acquisition, and situational awareness.
Cyber and Network-Centric Warfare: India has established new doctrines for cyberspace and amphibious operations.
The Battlefield Management System (BMS), currently in development, aims to create a real-time digital network that allows commanders to make precise, informed decisions based on live intelligence. This is a critical step in a future where information superiority is a key determinant of success.
Remaining Challenges
Despite these advances, several challenges remain that prevent the infantry from being fully prepared for next-generation combat.
Procurement Delays: The Indian defense procurement process has historically been slow and bureaucratic. This often leads to significant delays in the acquisition and deployment of new equipment, creating critical gaps in capabilities.
Technological Gaps: While India is pushing for indigenization, it still faces technological gaps in high-end defense systems and components. The country's defense budget, while large, allocates a limited portion to research and development, which hinders innovation.
Infrastructure and Training: Modernizing a military of 1.4 million personnel is a monumental task. Ensuring that all infantry units, especially those in remote and high-altitude areas, have access to the latest equipment, and are adequately trained in its use, remains a significant logistical and training challenge.
Fragmented Approach: While the F-INSAS program is comprehensive, its implementation has been fragmented. Critics have pointed out that the Army is still in the initial phases of this modernization, and bureaucratic inefficiencies have hampered its swift execution.
In conclusion, the Indian Army is well aware of the challenges posed by next-generation warfare and is taking decisive steps to equip its infantry for a multi-domain battlespace.
The F-INSAS program and the focus on indigenous technology are positive developments. However, to truly be ready for the threats of drones and cyber warfare, India needs to overcome its persistent challenges in procurement, budget allocation, and the full-scale integration of its modernization efforts.
Is India’s infantry adequately equipped for next-generation battlefield challenges, from drones to cyberwarfare?
India's infantry is undergoing a significant transformation to meet the challenges of modern warfare, but its readiness is a mix of promising advancements and persistent gaps.
The military recognizes that the traditional "foot soldier" must evolve into a "technology-empowered warfighter" to be effective on a modern battlefield dominated by drones, cyber threats, and network-centric operations.
Modernization Efforts and Strengths
The Indian Army's Futuristic Infantry Soldier as a System (F-INSAS) program is at the heart of this modernization drive.
It's a comprehensive initiative that aims to upgrade every aspect of the soldier's gear, from firepower to survivability and digital integration.
Upgraded Firepower: The Indian Army has been phasing out its long-standing INSAS rifles, which were known for their reliability issues, in favor of modern assault rifles like the Sig Sauer 716 and the AK-203.
This is a significant step towards improving the soldier's primary weapon. Additionally, the infantry is being equipped with advanced anti-tank guided missiles, precision-guided munitions, and modern grenade launchers to enhance their ability to engage enemy fortifications and armored threats.
Enhanced Survivability: The push for indigenous Level 6 body armor, which provides enhanced ballistic protection without excessive weight, is a crucial step towards better protecting soldiers.
The Defence Research and Development Organisation (DRDO) is also exploring the use of exoskeletons to increase endurance and reduce the physical burden on soldiers in difficult terrains.
Counter-Drone Capabilities: India is actively developing and deploying counter-drone systems to protect its infantry from the growing threat of unmanned aerial vehicles (UAVs) and loitering munitions. The "Bhargavastra" system, developed by a private Indian company, is a notable example. It is a multi-layered, low-cost system designed to detect and neutralize drone swarms with micro-missiles and rockets.
Furthermore, every infantry battalion is being equipped with a dedicated drone platoon to enhance reconnaissance, target acquisition, and situational awareness.
Cyber and Network-Centric Warfare: India has established new doctrines for cyberspace and amphibious operations.
The Battlefield Management System (BMS), currently in development, aims to create a real-time digital network that allows commanders to make precise, informed decisions based on live intelligence. This is a critical step in a future where information superiority is a key determinant of success.
Remaining Challenges
Despite these advances, several challenges remain that prevent the infantry from being fully prepared for next-generation combat.
Procurement Delays: The Indian defense procurement process has historically been slow and bureaucratic. This often leads to significant delays in the acquisition and deployment of new equipment, creating critical gaps in capabilities.
Technological Gaps: While India is pushing for indigenization, it still faces technological gaps in high-end defense systems and components. The country's defense budget, while large, allocates a limited portion to research and development, which hinders innovation.
Infrastructure and Training: Modernizing a military of 1.4 million personnel is a monumental task. Ensuring that all infantry units, especially those in remote and high-altitude areas, have access to the latest equipment, and are adequately trained in its use, remains a significant logistical and training challenge.
Fragmented Approach: While the F-INSAS program is comprehensive, its implementation has been fragmented. Critics have pointed out that the Army is still in the initial phases of this modernization, and bureaucratic inefficiencies have hampered its swift execution.
In conclusion, the Indian Army is well aware of the challenges posed by next-generation warfare and is taking decisive steps to equip its infantry for a multi-domain battlespace.
The F-INSAS program and the focus on indigenous technology are positive developments. However, to truly be ready for the threats of drones and cyber warfare, India needs to overcome its persistent challenges in procurement, budget allocation, and the full-scale integration of its modernization efforts.




_thumb.jpg)